 |
Chris Bell | 'A business that makes nothing but money is a poor business.' |
| - Henry Ford |
 |
Chris Bell | 'A business that makes nothing but money is a poor business.' |
| - Henry Ford |
SNHU - IT-640 - Telecommunications and Networking
Written by: Chris Bell - April, 2016
Intrusion detection and encryption is an important area to focus for big and small companies that are interconnected through a network. Hackers each have different motives but usually fall into categories that want email addresses, files downloaded to personal computers, personal information, and of course, money. These days, hackers arent like bank robbers that run inside for a few minutes and run back out to avoid being caught, instead they insert a program into your computer that watches and copies everything you do. That may not be the end of the world but when computers are connected to other computers through a network of cables and programming code, it can get much more complicated and gruesome for those within the network. There are a few areas of security that I'll research that include intrusion detection and encryption, in order to determine the best approach for a small company with less than 100 employees.
Risk assessment is becoming a factor for businesses to consider before making any decisions or changes to company processes and procedures. In fact, risk assessment has been instilled in us from our mothers since childhood because it's important to think before you act. Simple Network Management Protocol (SNMP) was built to be a simple protocol that uses SMI programming language to read and write, to and from, any device or operating system. However, security quickly became an issue, so SNMPv2 and SNMPv3 were new versions of the protocol that focused on security enhancements. "Apparently, risk wasn't one of the contributing factors when creating SNMP in 1988. SNMPv1 is notoriously inefficient at retrieving large amounts of management information, knowing no concept of scoping or bulk requests. It offers only minimal security, making it vulnerable to security threats, which effectively prevents SNMPv1 from being used to change the configuration of managed devices-in many cases, the risk of compromising the integrity of the network is simply too great. (Clemm, 2007)"
"A range of traditional crimes are now being perpetrated through cyberspace. This includes the production and distribution of child pornography and child exploitation conspiracies, banking and financial fraud, intellectual property violations, and other crimes, all of which have substantial human and economic consequences. (Department of Homeland Security, 2015)" The Internet was created to be interconnected, however it opens the doors for security issues because people can connect to your personal computer from anywhere in the world. A person in China can map their route to a New Hampshire PC similar to how a car can travel down many roads to get to another location.
"Of growing concern is the cyber threat to critical infrastructure, which is increasingly subject to sophisticated cyber intrusions that pose new risks. As information technology becomes increasingly integrated with physical infrastructure operations, there is increased risk for wide scale or high-consequence events that could cause harm or disrupt services upon which our economy and the daily lives of millions of Americans depend. (Department of Homeland Security, 2015)" As with anything else in the world, we figure out ways of securing banks from robberies, protecting the elderly from theft and children from harm, controlling individual privacy, and putting a stop to computer hacking.
Systems administrators cannot wait until something happens to protect against it, but instead must foresee the things that could happen and start protecting against them right away. "The preventive objective is to make it harder for attackers to get systems administration control, to slow them down so that they are easier to catch, and to make it easier to catch attacks when they occur. (Donaldson, Siegel, Williams, & Aslam, 2015)" Administrators can isolate networks to limit catastrophic intrusions, they can conduct regular audits of each system and infrastructure, and control access to portions of the system by job title and department. For example, there's no reason for the shipping department to have access to the accounting system, but they do in fact need access to inventory and customers' shipping information.
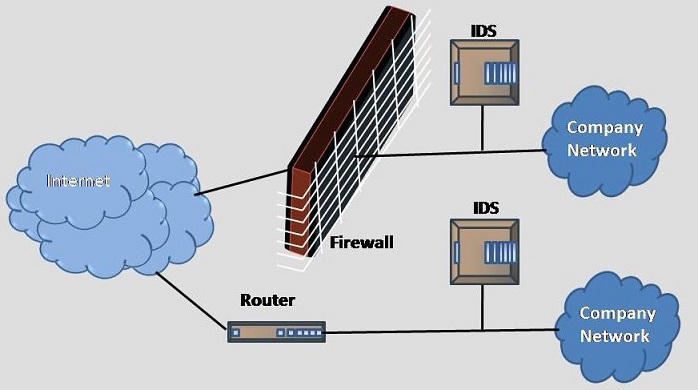
Network security capabilities provide preventive, detective, forensic, and audit functions on the enterprise network. "Network security technology or capability is not a "silver bullet" that will satisfy all cyber security requirements. However, an integrated set of capabilities can block, detect, and intercept many potential attacks. (Donaldson, Siegel, Williams, & Aslam, 2015)" Packet intercept and capture techniques (Wire Shark) can be used to monitor incoming and outgoing packets, along with additional programming code to detect malicious data. Setting up an SSL (Secure Sockets Layer) will open only a few doors (ports) for the data to travel through. It's important because it can be seen. Hacking through an SSL is like trying to steal something in Time Square during the middle of the day because you'll be seen more often than not. Firewalls and virtual machine firewalls are also important because they look for things that have already happened in the past, in which there is already a common solution that doesn't have to be re-invented.
There are security products that monitor and protect against intrusions such as identification and authentication software, access control software, and scanners that monitor access and behavior. Cryptography encrypts network traffic increases confidentiality of data passed between systems at the network level. "In a situation where Alice wants to communicate with Bob securely, "Alice encrypts her plain text message using an encryption algorithm so that the encrypted message, known as ciphertext, looks unintelligible to any intruder. (Kurose & Ross, 2013)" For example, each letter can be changed to the kth letter changing 'ABC' to 'KLM', with a private key of Ka. Bob will have a private key of Kb along with the access code to translate 'KLM' back to 'ABC'. This style of encrypting private information is called symmetric key encryption and decryption.
"Programs controlling whether users are allowed to delete files operate at the file system level of abstraction, rather than at the network packet level. In the intrusion detection product area, vendors have tended to focus on either the network level or the system level. (Escamilla, 1998)" It would be easy to protect against intrusions if we didn't care about letting people in, however we have to allow people who have access, and also somehow block all of the hackers. Similarly, banks need to let people in to conduct their banking, but also scan for robbers and stop them from entering.
How important is intrusion detection for your particular company? Is it worth protection costs of one million dollars per year or is it only worth ten thousand dollars per year? According to Wendy Nather, small companies can't afford what it really takes to protect a company infrastructure: "Here, in this study, the cost of what the CISOs have chosen as must-haves, along with someone to administer it, can cost as little as $300,000 to $400,000. If you went beyond bare bones, you are probably looking at $500k to $800k. This was based on a 1000-person organization. Doing the math, that means about $500 to $800 spent on security for every person in the organization" (Shimel, 2013)" This quickly gets into risk assessment and management. What are the risks of spending x, and if we spent 2x, how much lower would the risk assessment be? Is the risk worth the cost? When comparing security costs to budget constraints, it's clear that the accounting department would start to disagree with the network security department, so there's a balancing act that needs to address both money and risk.
Detecting an intrusion without having prevented it is like saying you saw a bank robbery. Detecting the robbery early will allow time to catch the criminal. Likewise, using intrusion detection techniques will slow the perpetrator down and possibly allow someone to catch him or her. Usually, preventative methods are created from a history of problems, but the 21st century requires us to prevent things from happening before we even know about it. IBM has a security network intrusion prevention system (IPS) in place which is a solution that detects, prevents, and chooses the correct hardware/software for each possibility. The IPS software can be installed inside or outside of the firewall, but IBM chooses to install it inside. "By deploying the network IPS inside the NAT (Network Address Translation) environment, all the events are reported with actual client IP addresses of the machines that are facing threats from the Internet. Additionally, with this type of deployment, an organization can define more specific custom blocking or exception rules. (Bucker, 2011)"
"Message integrity, end-point authentication and operational security are all involved in creating a secure communication between two people. Public key encryption involves a public key and private key for the sender and receiver. Rather than Bob and Alice sharing a single secret key (as in the case of symmetric key systems), Bob (the recipient of Alice's messages) instead has two keys - a public key that is known to everyone in the world (including Trudy the intruder) and private key that is known only to Bob. (Kurose & Ross, 2013)" The private key is needed to unlock the public key, but there are still issues that arise in terms of security. The public key is known to everyone, but intruders don't necessarily need a private key in order to use the public key to decrypt the message. "Trudy (the intruder) can thus mount a chosen plain-text attack, using the known standardized encryption algorithm and Bob's publicly available encryption key to encode any message she chooses. (Kurose & Ross, 2013)"
It's important to test the amount of scaling that's possible in terms of network bandwidth capacity, the number of segments to protect and the type of physical interfaces that are needed. For network segments where security is more important than availability, the IBM Security Network IPS can be instructed to not allow any traffic to pass uninspected. "When the appliance is configured to behave this way, an excess amount of traffic (more than it can inspect) results in the IBM Security Network IPS blocking some of the traffic without processing it, or rather, it fails closed to traffic. (Bucker, 2011)"
A credit card number is sensitive information that needs to be encrypted into letters instead of numbers, for example. Each #1 is equal to the letter A and each #2 is equal to letter B whereas (11212 = AABAB). When all credit card numbers are saved in an encrypted code hackers cannot pull all of the credit card numbers from a system. Instead, they could pull all of the encryptions from the database and must then figure out the code. According to news reporting originating in Chennai, India, by Vertical News journalists, research stated, "Privacy preservation and security provision against internal attacks in wireless mesh networks (WMNs) are more demanding than in wired networks due to the open nature and mobility of certain nodes in the network. Several schemes have been proposed to preserve privacy and provide security in WMNs. (Velayutham & Manimegalai, 2015)" "While there may be many algorithms that address these concerns, the RSA algorithm (named after its founders, Ron Rivest, Adi Shamir, and Leonard Adleman) has become almost synonymous with public key cryptography. RSA makes extensive use of arithmetic operations using modulo-n arithmetic. (Kurose, 2013)"
IT departments are comprised of teams that work on network security including cyber security, intrusion detection, intrusion prevention, encryption and cryptography, and much more. Before computers were invented there was still security detection and prevention, along with encryption of verbal passwords to pass through gate keepers. The cyber world is different, but still the same in many ways that require security and prevention of attacks. My research has shown that small companies have a hard time affording all that cybersecurity offers, however they should spend as much as their budget allows on data protection and encryption. Opening a bank without security is possible, but risky and vulnerable, so the perfect amount of security is that which stops hackers and doesn't bankrupt a company.
References:Bucker, A., Books24x7, I., & International Business Machines Corporation. International Technical Support Organization. (2011). Network intrusion prevention design guide: Using IBM security network IPS (1st ed.). United States: IBM, International Technical Support Organization.Clemm, A. (2007). Network management fundamentals. Indianapolis, IN: Cisco Press. Department of Homeland Security (September, 2015). Cybersecurity Overview. Retrieved from: https://www.dhs.gov/cybersecurity-overview Donaldson, S. E., Siegel, S. G., Williams, C. K., & Aslam, A. (2015). Enterprise cybersecurity: How to build a successful cyber defense program against advanced threats. New York: friends of ED, A press. Escamilla, T., & Books24x7, I. (1998). Intrusion detection: Network security beyond the firewall. New York: John Wiley. Kurose, J. F., & Ross, K. W. (2013). Computer networking: A top-down approach (6th ed.). Boston, MA: Pearson. Shimel, Alan (April, 2013). What is the Real Cost of Security? Retrieved from: http://www.networkworld.com/article/2224417/opensource-subnet/what-is-the-real-cost-of-security-.html Velayutham, R., & Manimegalai, D. (2015). CCMP advanced encryption standard cipher for wireless local area network (IEEE 802.11i): A comparison with DES and RSA. Journal of Computer Science, 11(2), 283. |