 |
Chris Bell | 'A business that makes nothing but money is a poor business.' |
| - Henry Ford |
 |
Chris Bell | 'A business that makes nothing but money is a poor business.' |
| - Henry Ford |
SNHU - IT-640 - Telecommunications and Networking
Written by: Chris Bell - April, 2016
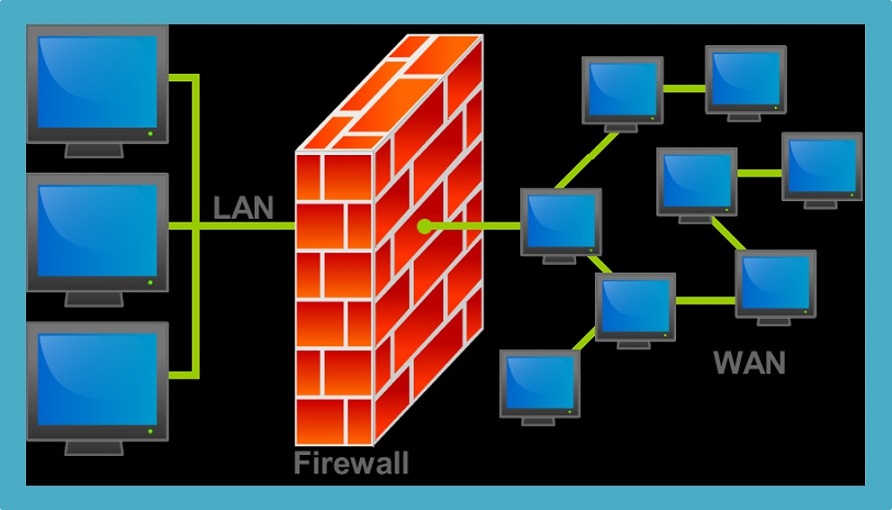
Firewalls block specific things from getting in while intrusion detection systems search for intruders and notify systems administrators when the system is breached. Firewalls are very black and white because the wall is up or down. All websites related to alcohol, tobacco, drugs, and pornography are blocked through a firewall within my company's network. However, there are instances when websites are blocked that might not have been necessary. Therefore, a firewall is similar to a volt at a bank because no one can get in without an access code. Intrusion detection systems are more similar to the officers staffed to watch the bank customers for possible abnormalities, intruders, and odd behavior. As the officers detect problems they dig deeper into the issue to, not only solve the issue, but also prevent it from happening in the future.
Firewalls are designed to provide a secure boundary between an untrusted network, such as the Internet, and a trusted network, such as your private corporate network (Escamilla, 1998). They use packet sniffers, sets of proxy servers, and a virtual private network (VPN), along with additional software such as virus scanners and log reporting tools, to successfully find perpetrators that don't have access to the system. Packet filters are installed as screening routers or bastion hosts. Both routers and bastion hosts are multi-homed, meaning that they have two or more network adapters. A router is a special-purpose computer that, in its simplest form, controls the flow of network packets between subnets. A bastion host is a general-purpose computer that has been hardened to remove unnecessary or security threatening software (Escamilla, 1998). A firewall security system for a home would be a force field around it that never lets anyone in. However, intrusion detection systems are more like security alarms that go off once the intruder enters the home.
IDS generally monitors any system held in three phases: the collection of audit data, the analysis of collected data and finally the release of an alert when a threat is detected, IDS can be classified in many different ways; the major classifications are: Active and Passive IDS, Network Intrusion detection systems (NIDS) and host Intrusion detection systems (HIDS), and finally, Knowledge-based (Signature-based) IDS and behavior-based (Anomaly-based) IDS (El-Taj, 2015). Intrusion detection systems have lists of “IF” statements that alert administrators, and also activate programs to stop an intrusion before a person sees it. IBM has their own hardware architecture that uses double Quad-Core Intel Xeon processors, noted in Chapter 3 of IBM Security Network IPS architecture, "Network-related communication is handled by a separate subsystem that employs dual communication-related processors. This system handles the network traffic and routes the traffic to the Main System for deep packet inspection. The Communication System uses its own proprietary operating system and drivers" The main system uses RAID-1 storage and an alert system that communicates the good and bad things back to the IBM Security Site Protector (Bucker, Books24x7, & IBM Corp., 2011).
Over the past few years, we have witnessed an ever increasing rampant battle between network managers & computer criminals which led to many developments in the tools used by both parties i.e. "legitimate computer professionals & computer criminals." Recently, interruption exposure & avoidance systems have earned increasing appreciation due to their more frequent involvement in the security domain since they allow security analysts to make fast reactions and thus take quick decisions to prevent any possible damage. This underlines the significance of upgraded detection & prevention processes, taking into consideration the competitive and dynamic network environment these days (El-Taj, 2015).
Both firewalls and IDPSs are both still needed in the industry. Design templates are common to use in web design because there's no need for developers to "reinvent the wheel." Similarly, firewalls are typically software created to be installed on a computer, so that it blocks typical intrusions that have been happening for years, such as Trojan, Worms, Spyware and Adware. Once installed, it does a good job of protecting what it was set to protect, however it doesn't improve along the way. IDPSs are set up like a firewall, but also managed on a regular basis by IT security departments for continuous improvement initiatives. When regular attacks continue to happen an expert could alter the code of a firewall, but usually make a revision to one of the IDS or IPS systems.
When someone realizes there's a new scam going around such as a criminal falsely dressed as an officer trying to gain access to homes, it would be nice to let everyone else in the world know about it. Snort is a public domain, open source IDS with hundreds of thousands of existing deployments. It uses the generic packet sniffing interface libpcap. Which is also used by Wireshark and many other packet sniffers (Kurose & Ross, 2013). Open source is a great way to utilize the mass amounts of people in the world without finding them, qualifying them, and later hiring them as employees. Mozilla Firefox and Wikipedia are both open source environments that compete well in their industries. Open source environments are making a name for themselves as conglomerate websites, and are building upon those models.
References:Bucker, A., Books24x7, I., & International Business Machines Corporation. International Technical Support Organization. (2011). Network intrusion prevention design guide: Using IBM security network IPS (1st ed.). United States: IBM, International Technical Support Organization. El-Taj, H. R. (2015). Intrusion detection and prevention systems (IDPS) state of art: IDPS challenges. International Journal of Computer Science and Information Security, 13(9), 28. Escamilla, T., & Books24x7, I. (1998). Intrusion detection: Network security beyond the firewall. New York: John Wiley. Kurose, J. F., & Ross, K. W. (2013). Computer networking: A top-down approach (6th ed.). Boston, MA: Pearson. |